Mobile profiling and surveillance
The world of digital mobile communications operates on largely similar principles to the Internet. Your mobile device has a unique number, received its connection from a regional intermediary and all communications are routed through a central gateway. Internet connected mobile phones have bridged the divide even closer.
Let's have a look at the details recorded by the telecommunications network when you are using your mobile phone. Every handset is identified on the network by a unique IMEI number (you can see what your phone's IMEI number is by pressing ….). You are able to register on the network and make/receive calls once your SIM card number is approved. This is the same as your telephone number and allows you to operate on the network.
Whenever your phone is switched on and receives a signal, it must keep in constant communication with a mobile telephone tower. You can see these towers on tall buildings and mountain tops, spaced several kilometres apart. Your telephone sends out a signal and is answered by the nearest three available towers. It will use the tower closest to it and regularly update the proximity by sending out another signal every second or so. Notice that when you are talking on the phone in a moving car, you sometimes lose signal for a few seconds – this is your phone changing tower's as its location changes.
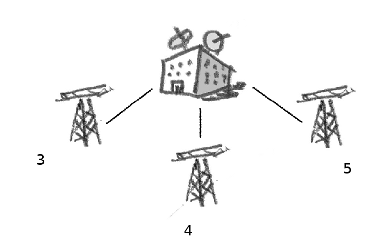
On the diagram above, you can see the amount of milliseconds between a telephone tower and (your) mobile phone. The closest tower (3) will be chosen. However, knowing the distance between the phone and three separate towers allows for triangulation – a mathematical process that can pinpoint the location of your phone to within a few square metres.
To recap, every second your phone communicates its unique identification number, the SIM registration details and its location. In most countries, mobile phone providers must record and keep these details for several years – not your conversations, but what is known as network data. The same applies for phone calls you make or receive from the handset. The sender's and recipient's number, the date and duration of the call, the location of the two handsets, all of this information is recorded and stored.
Its quite difficult to get away from the reality. In some countries, pre-paid SIM cards can be purchased anonymously (without registering your identity). There are also services to spoof or fake the handsets IMEI – however this is illegal in most jurisdictions. All communications made through a mobile phone network are also vulnerable to surveillance, with ever improving software able to decode and decipher certain words and phrases from the digital stream.
The introduction of Internet enabled mobile phones have restored a little bit of communications privacy to the cellular network. You can use Internet encryption protocols (namely SSL) to create a secure connection between your handset and the provider of the service (e.g. Gmail) just as you would using a standard computer. This means that you would have more privacy sending an email message rather than a text from your mobile phone. The latest developments for mobile based communications privacy is encrypted Voice Over IP (VoIP) tools. Some countries allow mobile users to run Skype. Other tools such as CSIPSimple allow end-to-end encryption for voice calls made from mobile phones.