Circumventing Censorship
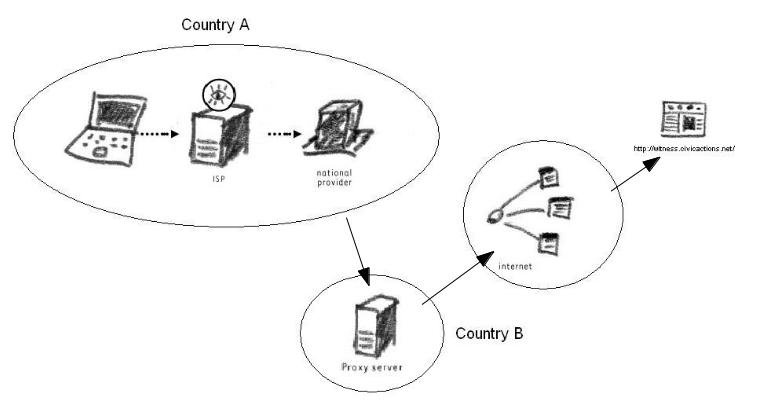
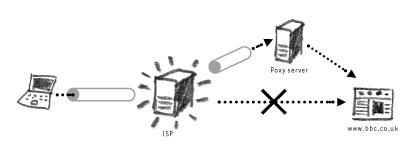
If you are not allowed to access www.bbc.co.uk in your country, you can ask another computer (a proxy) to fetch the website for you. This proxy will be located in a different country that is not restricted by the censorship rules of your Internet environment. To the censor, you will simply be accessing a computer (or website) that is not present in their filtering lists.
There are thousands of such proxy services, set up in many different ways and for different purposes, albeit performing a similar function – to be the intermediary between a client's computer and a host website.
Media: Read through https://flossmanuals.net/bypassing-censorship/ch010_simple-tricks/ to get an idea of how to bypass censorship using third-party webservices and some simple tricks. Anonymisers
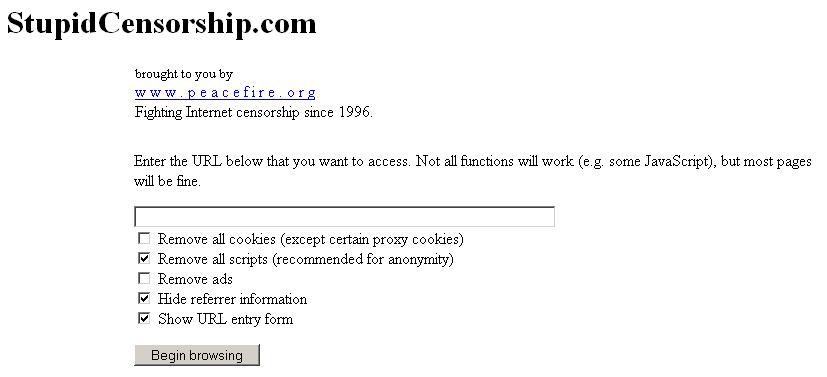
The simplest type of proxy server to use is also known as an anonymiser. The coding for proxy server operations is built into a webpage , through which you can browse the Internet directly. Originally created to hide your true location from the website visited, they also function to conceal your true destination on the Internet.
When using anonymisers, the visited website does not know the origin (the real IP address) of your computer. The ISP does not know your true destination
Their popularity, however, has led many countries that practice Internet filtering to block access to these sites as well.
Note: Bear in mind that if your Internet connection to the anonymiser could be made over an open channel (HTTP as opposed to HTTPS – see Section 1: Encrypted connections for email and Internet browsing for more explanation), the data sent and received through this service is not protected from surveillance. It is advisable to always use encrypted anonymisers and other proxy services so as to protect the fact that you are circumventing a blocklist from the provider.
Virtual Private Networks
Another way to bypass Internet censorship is with the use of virtual private networks (VPNs). This basically refers an office network extended across the Internet. Many organisations use VPNs when they want staff to have access to network drives and internal resources, whilst not present in the office. VPN's create encrypted connections to the central server and route all information sent and received from the computer through this connection. Hence, if your VPN server is located in a country that does not practice Internet censorship, you may use this service to route Internet traffic through.
HotSpot Shield is one example of a free VPN service to be used for secure Internet browsing and circumvention . You will be provided with login details and software with which to connect to their servers with.
Exercise: Download and install https://www.hotspotshield.com/
Anonymity Networks
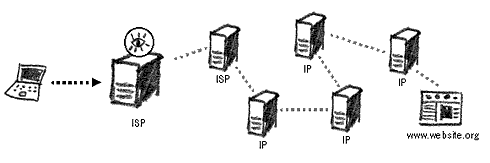
Anonymity networks typically 'bounce' your Internet traffic around various secure proxies in order to disguise where you are coming from and what you are trying to access. This can significantly reduce the speed at which you are able to load websites and other Internet services. One such network is Tor (http://torproject.org) an abbreviation for The onion router, with an interface in many different languages and a huge team of supporters and contributors around the world. Originally developed by the US Naval Research Laboratory to assist defense and intelligence services in anonymous Internet browsing, it is currently maintained by a worldwide collective of security and anonymity specialists.
Tor relies on a large network of servers, provided by volunteers around the world. There are currently around a thousand such servers. When you join this network, your create a random circuit passing through three or more Tor servers, negotiating a separate set of encryption keys for each along the way. This ensures that no single server used to create your circuit can trace your final and original destination. Imagine that you send a letter to a friend and package it in several different envelopes writing a different address on each one. The letter will be sent around and not one of the addressees along the route will know both the origin and final destination of the letter, but only the previous address it came from and the next one it will be going to. Should any of the addressees wish to open the letter, they would not be able to read its content, as it will be encrypted with a password that relies on other two addressees (servers) to decode.
You may also use a mobile version of Tor, called Tor Browser. It does not need to be installed on your computer and can be carried around on a USB memory stick, useful for Internet cafes and when using other people's computers. It comes pre-configured with its own Internet browser already set to use the anonymity network.
Tor is a useful tool to bypass censorship, but its strong anonymity becomes a disadvantage when publishing, say, on Wikipedia. You will need to investigate first if your desired website will function with Tor. Also, do not use it to log into insecure Internet accounts (e.g http://mail.ru). Tor protects your anonymity, not the privacy of your connection – the last server in your route will have unrestricted access to your traffic. As always, you must ensure that you have an encrypted connection, using HTTPS, to a secure website before exchanging sensitive information, such as passwords and emails, through a browser.