| (7 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
| − | In what become known as the Crypto Wars, “...for several decades, individuals and organizations concerned with protecting their personal privacy and corporate secrets have been engaged in a heated battle with government officials to gain the right to freely employ encryption techniques and technologies to safeguard their information.” Eventually a layer of encryption was built into the Internet's infrastructure to allow for secure connections between two computers. It is called the Secure Sockets Layer and is often abbreviated to SSL. The advantage of using SSL in webmail services is that the technology is already built into the framework of the Internet and does not require any additional tools or action from the user. Companies and non-profit | + | In what become known as the Crypto Wars, “...for several decades, individuals and organizations concerned with protecting their personal privacy and corporate secrets have been engaged in a heated battle with government officials to gain the right to freely employ encryption techniques and technologies to safeguard their information.” Eventually a layer of encryption was built into the Internet's infrastructure to allow for secure connections between two computers. It is called the Secure Sockets Layer and is often abbreviated to SSL. The advantage of using SSL in webmail services is that the technology is already built into the framework of the Internet and does not require any additional tools or action from the user. Companies and non-profit organizations can (and often do) offer webmail services protected by SSL connections. It is the minimum requirement today for a degree of privacy in email and Internet communication. |
[[File:SSL.png|SSL]] | [[File:SSL.png|SSL]] | ||
| Line 14: | Line 14: | ||
{{#ev:youtube|zPqtx1J6udc}} | {{#ev:youtube|zPqtx1J6udc}} | ||
| − | + | '' '''Note:''' Email is a medium where the receiver of your message is responsible for your privacy. Imagine you are using an SSL enabled webmail service and your recipient is using an insecure webmail provider. When they read your message, it will be accessible to the recipient's Internet Service Provider and at the national gateway of the country they reside in. Pay careful attention to the providers used by your email's recipient.'' | |
| − | + | ||
| − | + | ||
| − | Note: Email is a medium where the receiver of your message is responsible for your privacy. Imagine you are using an SSL enabled webmail service and your recipient is using an insecure webmail provider. When they read your message, it will be accessible to the recipient's Internet Service Provider and at the national gateway of the country they reside in. Pay careful attention to the providers used by your email's recipient. | + | |
| − | + | ||
[[File:webmail.jpg|webmail]] | [[File:webmail.jpg|webmail]] | ||
| Line 24: | Line 20: | ||
It is advisable for both parties to use the same SSL webmail service provider. Email, traveling on the Internet between servers, is usually unencrypted and can easily be intercepted. Keep in mind that even though your connection to the server is encrypted, the message itself is sent unprotected through this connection. This means that the webmail service provider will have access to your messages. Perhaps this is not a game changer for you, nevertheless you should be aware of it. | It is advisable for both parties to use the same SSL webmail service provider. Email, traveling on the Internet between servers, is usually unencrypted and can easily be intercepted. Keep in mind that even though your connection to the server is encrypted, the message itself is sent unprotected through this connection. This means that the webmail service provider will have access to your messages. Perhaps this is not a game changer for you, nevertheless you should be aware of it. | ||
| − | Note: A 'Man-in-the-Middle' attack poses one of the biggest threats to using SSL securely. The topic is explained in more detail in the Digital Security and Privacy manual and (as always) in Wikipedia. | + | '' '''Note:''' A 'Man-in-the-Middle' attack poses one of the biggest threats to using SSL securely. The topic is explained in more detail in the Digital Security and Privacy manual and (as always) in Wikipedia. '' |
The ability to protect your information further by encrypting its content before it leaves the computer can be done manually by using tools such as PGP/GPG. This is the best (and the security expert's choice) way to ensure that no one interferes with your communications and your message can only ever be read by its intended recipient. Public key encryption may not come naturally to you and there are services which will perform the complicated processes for you (for this reason they are not liked by some security experts). | The ability to protect your information further by encrypting its content before it leaves the computer can be done manually by using tools such as PGP/GPG. This is the best (and the security expert's choice) way to ensure that no one interferes with your communications and your message can only ever be read by its intended recipient. Public key encryption may not come naturally to you and there are services which will perform the complicated processes for you (for this reason they are not liked by some security experts). | ||
| Line 30: | Line 26: | ||
[[File:mailencryption.jpg|mail encryption]] | [[File:mailencryption.jpg|mail encryption]] | ||
| − | Media: Public key cryptography explained | + | '''Media:''' Public key cryptography explained |
{{#ev:youtube|3QnD2c4Xovk}} | {{#ev:youtube|3QnD2c4Xovk}} | ||
Latest revision as of 18:52, 27 May 2014
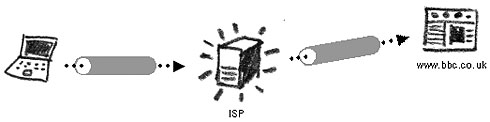
In what become known as the Crypto Wars, “...for several decades, individuals and organizations concerned with protecting their personal privacy and corporate secrets have been engaged in a heated battle with government officials to gain the right to freely employ encryption techniques and technologies to safeguard their information.” Eventually a layer of encryption was built into the Internet's infrastructure to allow for secure connections between two computers. It is called the Secure Sockets Layer and is often abbreviated to SSL. The advantage of using SSL in webmail services is that the technology is already built into the framework of the Internet and does not require any additional tools or action from the user. Companies and non-profit organizations can (and often do) offer webmail services protected by SSL connections. It is the minimum requirement today for a degree of privacy in email and Internet communication.
The existence and properties of an SSL connection to a particular website can be identified by two distinguishing features:
The address for the website will begin with https:// (the 's' standing for secure!) A little padlock will appear in the address bar or on bottom toolbar, depending on your Internet browser
This means that the website you are visiting and your Internet browser have agreed upon an encrypted communications channel. You can click on the padlock to view the details of this secure connection.
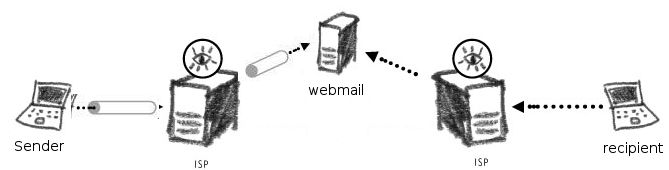
Note: Email is a medium where the receiver of your message is responsible for your privacy. Imagine you are using an SSL enabled webmail service and your recipient is using an insecure webmail provider. When they read your message, it will be accessible to the recipient's Internet Service Provider and at the national gateway of the country they reside in. Pay careful attention to the providers used by your email's recipient.
It is advisable for both parties to use the same SSL webmail service provider. Email, traveling on the Internet between servers, is usually unencrypted and can easily be intercepted. Keep in mind that even though your connection to the server is encrypted, the message itself is sent unprotected through this connection. This means that the webmail service provider will have access to your messages. Perhaps this is not a game changer for you, nevertheless you should be aware of it.
Note: A 'Man-in-the-Middle' attack poses one of the biggest threats to using SSL securely. The topic is explained in more detail in the Digital Security and Privacy manual and (as always) in Wikipedia.
The ability to protect your information further by encrypting its content before it leaves the computer can be done manually by using tools such as PGP/GPG. This is the best (and the security expert's choice) way to ensure that no one interferes with your communications and your message can only ever be read by its intended recipient. Public key encryption may not come naturally to you and there are services which will perform the complicated processes for you (for this reason they are not liked by some security experts).
Media: Public key cryptography explained