Difference between revisions of "Information storage"
| (One intermediate revision by one other user not shown) | |||
| Line 1: | Line 1: | ||
Computer and flash disk theft and confiscation is still the preferred method of security agencies around the world to get at activists' data. | Computer and flash disk theft and confiscation is still the preferred method of security agencies around the world to get at activists' data. | ||
| − | Media: How to get into any Windows computer without a password. The camera is a little shaky on this video but you'll get the idea. | + | '''Media:''' How to get into any Windows computer without a password. The camera is a little shaky on this video but you'll get the idea. |
| + | |||
| + | {{#ev:youtube|0qAf6u7itvY}} | ||
| − | |||
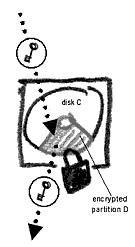
Encrypting your information is a bit like keeping it in a locked safe. Only those who have a key or know the lock's combination (usually a password that unlocks the encryption) can access it. The analogy is particularly appropriate for TrueCrypt which creates encrypted containers called 'volumes' rather than simply protecting one file at a time. | Encrypting your information is a bit like keeping it in a locked safe. Only those who have a key or know the lock's combination (usually a password that unlocks the encryption) can access it. The analogy is particularly appropriate for TrueCrypt which creates encrypted containers called 'volumes' rather than simply protecting one file at a time. | ||
| Line 9: | Line 10: | ||
You then simply store all your private data (or all your data) in this volume and it will be protected from unauthorised access by strong encryption and your chosen password. The advantage of this system is that data encryption (and decryption) happens automatically and does not require any extra action from the user. Simply copying the files to the container will encrypt them and moving them to another disk or attaching them to an email message say, will decrypt them. This is called encryption-on-the-fly and allows you to operate with your encrypted documents as you would with any other file on your computer. | You then simply store all your private data (or all your data) in this volume and it will be protected from unauthorised access by strong encryption and your chosen password. The advantage of this system is that data encryption (and decryption) happens automatically and does not require any extra action from the user. Simply copying the files to the container will encrypt them and moving them to another disk or attaching them to an email message say, will decrypt them. This is called encryption-on-the-fly and allows you to operate with your encrypted documents as you would with any other file on your computer. | ||
| − | |||
| − | + | [[File:encrypting4.png|encrypting 4]] | |
| − | |||
| − | + | {{#ev:youtube|alQj1Xxmpdk}} | |
| + | |||
| + | '' '''Note:''' TrueCrypt has three different options for creating a secure storage space on your computer or media device. You can create a file container, encrypt an existing disk partition or encrypt the entire computer. Even though full computer encryption may seem the most attractive choice, it is also the riskiest. If something goes wrong in the operating system's internal functions, your computer may never boot again and would need to be formatted. Encrypting a disk partition (disk D: for example) is possible only if such a partition already exists (and is empty) or will require you to split your main disk into two partitions – also not a trivial task.'' | ||
| + | |||
| + | '''Exercise:''' Go through the https://security.ngoinabox.org/en/truecrypt_main.html chapter to set up an encrypted partition. Practice moving files in an out of the encrypted container. | ||
'''Hidden Volumes''' | '''Hidden Volumes''' | ||
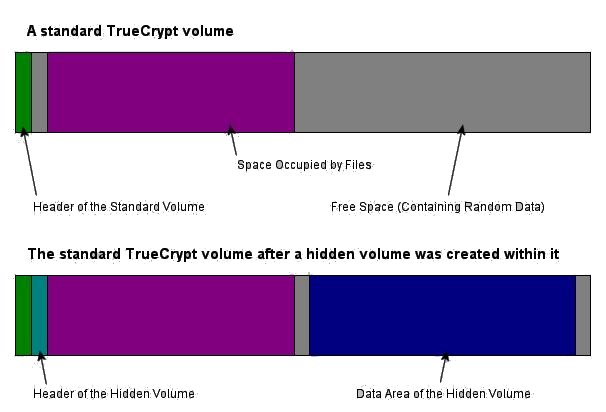
As a remedy to this situation TrueCrypt offers the hidden volume feature. Think of it as a false bottom in your encrypted suitcase. If the adversary forces or intimidates you into surrendering the volume's password, you can, and they will have access the outer volume, but not the information that you truly care about protecting. This will be stored inside a hidden volume. TrueCrypt developers call this feature plausible deniability as there is no technical way to prove that a false bottom exists. It all depends on your strategy and the 'decoy' information that you choose to store in the outer volume. | As a remedy to this situation TrueCrypt offers the hidden volume feature. Think of it as a false bottom in your encrypted suitcase. If the adversary forces or intimidates you into surrendering the volume's password, you can, and they will have access the outer volume, but not the information that you truly care about protecting. This will be stored inside a hidden volume. TrueCrypt developers call this feature plausible deniability as there is no technical way to prove that a false bottom exists. It all depends on your strategy and the 'decoy' information that you choose to store in the outer volume. | ||
| − | + | [[File:truecrypt.jpg|true crypt]] | |
| + | |||
| + | '''From the TrueCrypt user guide:''' "It may happen that you are forced by somebody to reveal the password to an encrypted volume. There are many situations where you cannot refuse to reveal the password (for example, due to extortion). Using a so-called hidden volume allows you to solve such situations without revealing the password to your volume." | ||
| + | |||
| + | '''Important:''' The hidden disk is created inside an existing (outer) volume. Psychically it is located within the outer volume's free space, or you could imagine it as being located at the end of the outer volume. Note the hidden volume's size and always remember that your outer volume must have enough free space to host the hidden one. | ||
| + | {{#ev:youtube|5hPPxTuEaok}} | ||
| − | + | '''Exercise:''' Go through the https://security.ngoinabox.org/en/truecrypt_hiddenvolumes.html to create a hidden volume inside your existing volume from the previous section. Practice moving files in an out of the hidden volume, as well as mounting the outer and the hidden volume. | |
| − | + | '''Note:''' The strategy behind using a hidden volume relies on the quality of the 'decoy' data that you wish to store inside the outer volume. This must be good enough to satisfy the adversary. The data has to be relevant and frequently updated. It should convince the adversary that they have broken your defense and there is no need to press you further. | |
| − | + | '''Exercise:''' Prepare your outer volume with data that will satisfy your adversary. | |
| − | + | '''Editorial note: '''In May of 2014 the [http://truecrypt.sourceforge.net/ TrueCrypt website] announced the project was ceasing development following the discovery of a serious security vulnerability in the code. Users were recommended to find an alternative solution. However since that time, an [https://opencryptoaudit.org/ independent, open source project] to audit the software has been undertaken and the [https://wiki.ciphershed.org/Audit subsequent review] of this audit concludes: | |
| − | + | "The remaining issues are less severe, but still important enough to at least do the "short term fix" in Phase 1. They are issues like integer overflows and errors in the kernel driver checking file permissions and names. They are real security holes, but assuming there is only one user on the machine and no malware to exploit the holes (big IF), then they should not cause problems. | |
| − | + | After reading this audit, we would recommend that TrueCrypt 7.1a remains safe for use" | |
Latest revision as of 21:01, 18 July 2014
Computer and flash disk theft and confiscation is still the preferred method of security agencies around the world to get at activists' data.
Media: How to get into any Windows computer without a password. The camera is a little shaky on this video but you'll get the idea.
Encrypting your information is a bit like keeping it in a locked safe. Only those who have a key or know the lock's combination (usually a password that unlocks the encryption) can access it. The analogy is particularly appropriate for TrueCrypt which creates encrypted containers called 'volumes' rather than simply protecting one file at a time.
You then simply store all your private data (or all your data) in this volume and it will be protected from unauthorised access by strong encryption and your chosen password. The advantage of this system is that data encryption (and decryption) happens automatically and does not require any extra action from the user. Simply copying the files to the container will encrypt them and moving them to another disk or attaching them to an email message say, will decrypt them. This is called encryption-on-the-fly and allows you to operate with your encrypted documents as you would with any other file on your computer.
Note: TrueCrypt has three different options for creating a secure storage space on your computer or media device. You can create a file container, encrypt an existing disk partition or encrypt the entire computer. Even though full computer encryption may seem the most attractive choice, it is also the riskiest. If something goes wrong in the operating system's internal functions, your computer may never boot again and would need to be formatted. Encrypting a disk partition (disk D: for example) is possible only if such a partition already exists (and is empty) or will require you to split your main disk into two partitions – also not a trivial task.
Exercise: Go through the https://security.ngoinabox.org/en/truecrypt_main.html chapter to set up an encrypted partition. Practice moving files in an out of the encrypted container.
Hidden Volumes As a remedy to this situation TrueCrypt offers the hidden volume feature. Think of it as a false bottom in your encrypted suitcase. If the adversary forces or intimidates you into surrendering the volume's password, you can, and they will have access the outer volume, but not the information that you truly care about protecting. This will be stored inside a hidden volume. TrueCrypt developers call this feature plausible deniability as there is no technical way to prove that a false bottom exists. It all depends on your strategy and the 'decoy' information that you choose to store in the outer volume.
From the TrueCrypt user guide: "It may happen that you are forced by somebody to reveal the password to an encrypted volume. There are many situations where you cannot refuse to reveal the password (for example, due to extortion). Using a so-called hidden volume allows you to solve such situations without revealing the password to your volume."
Important: The hidden disk is created inside an existing (outer) volume. Psychically it is located within the outer volume's free space, or you could imagine it as being located at the end of the outer volume. Note the hidden volume's size and always remember that your outer volume must have enough free space to host the hidden one.
Exercise: Go through the https://security.ngoinabox.org/en/truecrypt_hiddenvolumes.html to create a hidden volume inside your existing volume from the previous section. Practice moving files in an out of the hidden volume, as well as mounting the outer and the hidden volume.
Note: The strategy behind using a hidden volume relies on the quality of the 'decoy' data that you wish to store inside the outer volume. This must be good enough to satisfy the adversary. The data has to be relevant and frequently updated. It should convince the adversary that they have broken your defense and there is no need to press you further.
Exercise: Prepare your outer volume with data that will satisfy your adversary.
Editorial note: In May of 2014 the TrueCrypt website announced the project was ceasing development following the discovery of a serious security vulnerability in the code. Users were recommended to find an alternative solution. However since that time, an independent, open source project to audit the software has been undertaken and the subsequent review of this audit concludes:
"The remaining issues are less severe, but still important enough to at least do the "short term fix" in Phase 1. They are issues like integer overflows and errors in the kernel driver checking file permissions and names. They are real security holes, but assuming there is only one user on the machine and no malware to exploit the holes (big IF), then they should not cause problems.
After reading this audit, we would recommend that TrueCrypt 7.1a remains safe for use"