Difference between revisions of "How does the Internet actually work?"
(→Internet Routing) |
|||
| (49 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
| − | Connect | + | =Connect= |
| − | + | ||
| + | ==Internet Routing== | ||
| + | <br> | ||
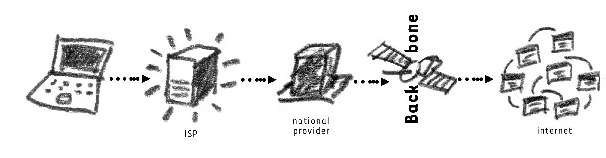
'Going online' requires connecting your computer to the national Internet infrastructure. The process begins by establishing a link to your Internet Service Provider (ISP) whether through a telephone line, cable or wireless connection. The ISP connects you to the national infrastructure which is regulated and in some countries governed by the ministry of telecommunications. Using one (or one of several) Internet exchange points in your country, the connection is routed to the global Internet. | 'Going online' requires connecting your computer to the national Internet infrastructure. The process begins by establishing a link to your Internet Service Provider (ISP) whether through a telephone line, cable or wireless connection. The ISP connects you to the national infrastructure which is regulated and in some countries governed by the ministry of telecommunications. Using one (or one of several) Internet exchange points in your country, the connection is routed to the global Internet. | ||
| − | + | [[File:InternetConnectionsshort.jpg|InternetConnections]] | |
| − | [[File: | + | |
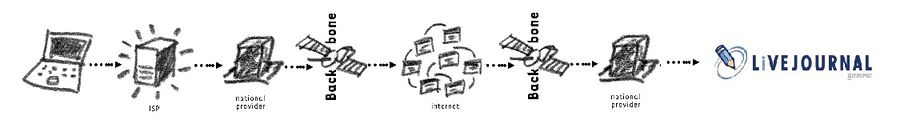
| + | Whether you are accessing the Internet from your home computer or from a mobile phone on a moving train, the principle remains the same: your device connects to the local ISP > connects to the national provider > connects to the Internet exchange (backbone). Should you be visiting a website or sending an email to a server located in a different country (quite likely) then this progression through the network hierarchy is repeated on the other end side of the communications channel too. | ||
| − | |||
| + | [[File:InternetConnections.jpg|900px|InternetConnections]] | ||
| − | |||
Notice that in the last example, your connection routes through at least two national (legal) jurisdictions. | Notice that in the last example, your connection routes through at least two national (legal) jurisdictions. | ||
| − | Exercise: Use a Geo-IP traceroute tool (http://traceroute.monitis.com/ ) to view how your connection is routed to a particular website. | + | '''Exercise:''' Use a Geo-IP traceroute tool (http://traceroute.monitis.com/ ) to view how your connection is routed to a particular website. |
| − | Note: The Internet is a packet-switching network. This means that your email, for example, is broken down into small individual packets which are then sent independently of each other along the many possible routes on the network that connect you to your friend's computer. These packets are then reassembled at the receiver's end to re-create your email. Important! You do not control how data travels through the Internet once you hit the send button. | + | '' '''Note:''' The Internet is a packet-switching network. This means that your email, for example, is broken down into small individual packets which are then sent independently of each other along the many possible routes on the network that connect you to your friend's computer. These packets are then reassembled at the receiver's end to re-create your email. Important! You do not control how data travels through the Internet once you hit the send button. '' |
| − | Locate | + | |
| + | =Locate= | ||
Now that you're connected, let's discuss what happens when you request to open a particular website and how this site then delivers back to your computer. Numerous protocols and technical standards govern how the Internet and all of its users locate and communicate with each other. The most important of which we will discuss has to do with Internet addressing. Because everyone on the Internet adheres to these, you are able to open webiste.com and send an email from your computer to a friend's mobile phone in another country. | Now that you're connected, let's discuss what happens when you request to open a particular website and how this site then delivers back to your computer. Numerous protocols and technical standards govern how the Internet and all of its users locate and communicate with each other. The most important of which we will discuss has to do with Internet addressing. Because everyone on the Internet adheres to these, you are able to open webiste.com and send an email from your computer to a friend's mobile phone in another country. | ||
| − | + | ||
| + | ==Internet Protocol (IP) Address== | ||
Internet routing is possible because every computer is uniquely identified on the network by what is known as an IP address. These addresses look like 83.169.39.231 and are the building blocks of Internet addressing. Whenever you want to open a website from your computer, the Internet needs to know your IP address and the IP address of the server the website is hosted on, to make the connection. Important! Your IP address is assigned to you by your local ISP or if you are using mobile Internet, by your telecommunications provider. In most countries ISPs are obligated by law to collect and store traffic data (which IP requested a connection to which IP and when) . This is used primarily for identifying user activity on the Internet at a later date and is the main tool in the hands of Internet police. | Internet routing is possible because every computer is uniquely identified on the network by what is known as an IP address. These addresses look like 83.169.39.231 and are the building blocks of Internet addressing. Whenever you want to open a website from your computer, the Internet needs to know your IP address and the IP address of the server the website is hosted on, to make the connection. Important! Your IP address is assigned to you by your local ISP or if you are using mobile Internet, by your telecommunications provider. In most countries ISPs are obligated by law to collect and store traffic data (which IP requested a connection to which IP and when) . This is used primarily for identifying user activity on the Internet at a later date and is the main tool in the hands of Internet police. | ||
| − | Note: in an office or Internet cafe scenario, only one computer is connected to the Internet and all other computers connect through it. Only the Internet facing computer (modem) is assigned an external IP address, whilst the others are assigned an internal IP address. Browsing history made from a computer in an Internet café can be traced back by the ISP to the café, not to the individual's computer. | + | '''Note:''' in an office or Internet cafe scenario, only one computer is connected to the Internet and all other computers connect through it. Only the Internet facing computer (modem) is assigned an external IP address, whilst the others are assigned an internal IP address. Browsing history made from a computer in an Internet café can be traced back by the ISP to the café, not to the individual's computer. |
| + | |||
| + | '''Exercise: Find your current IP on the Internet''' | ||
| + | |||
| + | #View your computer's IP by visiting http://hostip.info You can also view the IP addresses associated with your favourite websites through this system. | ||
| + | #Next, go to http://whois.net/ to find out who that particular IP address is registered to. | ||
| − | + | ==Domain Name System== | |
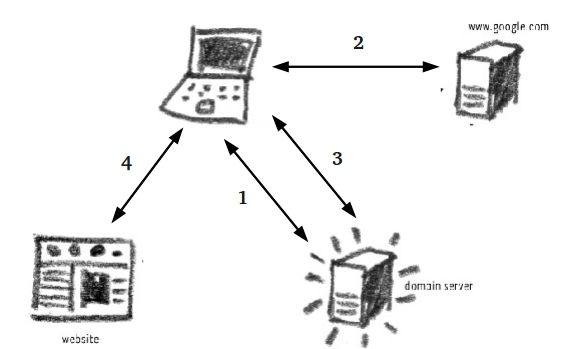
| − | + | Even though all computers connected to the Internet are assigned an IP address, we usually do not know these addresses nor do we use them when opening a website. Numbers are quite difficult to remember (how many phone numbers do you know by heart?) and for this reason we assign names as addresses for our websites (also known as a Universal Resource Locator – URL). These names and their associated IP addresses are recorded in the Domain Name System (DNS). This is akin to the Internet's telephone directory and is another critical component of Internet routing and operations. DNS is hierarchical, meaning that your computer can have its list of URLs and corresponding IPs, your ISP will have a list, the national provider will have a list and so on, right up to the root DNS servers (of which there are 13). Should your computer not have an entry for www.livejournal.com it will ask the next list up in line – the ISP's and so on. Whether browsing websites or sending email, DNS always plays a part. Below is a diagram describing how DNS is utilized when you search for the LiveJournal website. | |
| − | |||
| − | + | [[File:DSNDiag.jpg|DSNDiag]] | |
| − | |||
| + | * Not knowing the LiveJournal address, you open Google naturally. Your computer doesn't know where www.google.com is and so asks the DNS server for Google's IP. | ||
| + | * Using Google's IP you locate the search engine and punch in 'LiveJournal'. The search returns www.livejournal.com which you promptly click. | ||
| + | * Once again, your computer has no idea where to locate www.livejournal.com and returns to the DNS server to get its IP. | ||
| + | * Finally, using the correct IP you can access LiveJournal's website. | ||
| − | |||
| + | '''Media:''' A brief explanation how websites are located using the DNS. | ||
| + | {{#ev:youtube|oN7ripK5uGM}} | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | Another video that discusses the regulative and technical framework behind DNS and why this is important. | |
| + | {{#ev:youtube|72snZctFFtA}} | ||
| − | |||
| − | + | '''Exercise: Change your computer's DNS settings''' (Here is a walkthrough regarding changing DNS settings in Windows 7) | |
| + | #Use the http://hostip.info tool to find out the IP addresses of your favourite websites. | ||
| + | #Open the Control Panel and locate your Network Connection settings (LAN or Wireless). | ||
| + | #Manually set the DNS servers to OpenDNS addresses: | ||
| − | |||
| − | + | 208.67.222.222 | |
| + | 208.67.220.220 | ||
| − | |||
| − | |||
| − | |||
| − | + | or use two of the root DNS servers http://en.wikipedia.org/wiki/Root_name_server ). | |
| − | + | =Interact= | |
| − | + | The last part of the Internet's infrastructure concerns the applications we use to send and receive content on the Internet. These include your browser, email program, chat client and every other software on your computer that utilizes or help you interact on the Internet. Every application has its particular language and protocols and these often affect how information is transmitted between two computers on the Internet. This usually involves a type of technical language (protocol) by which it communicates or the channel (port) it selects for communication. For example, some applications send data in a clear-text format and every computer/router that stands in-between the communicating parties can access and understand the transmitted information. Other applications take special care to ensure privacy for the communicating parties. For example, when you connect to http://google.com your browser is using the 'http' protocol on port 80. However when the website's address is preceded by the letters 'https' (https://mail.google.com) your browser begins to use the Secure Sockets Layer (SSL) protocol on port 443. The majority of this course is explaining and exploring the different ways that applications interact on the Internet, directly impacting upon your privacy, anonymity and authentication of the transmitted message. | |
| + | '''Media:''' Here's a video tutorial from some kid in his bedroom, pulling all the topics that we have discussed above, together. | ||
| − | + | {{#ev:youtube|ZGRjUhBj5gg}} | |
Latest revision as of 22:54, 2 June 2014
Contents
Connect
Internet Routing
'Going online' requires connecting your computer to the national Internet infrastructure. The process begins by establishing a link to your Internet Service Provider (ISP) whether through a telephone line, cable or wireless connection. The ISP connects you to the national infrastructure which is regulated and in some countries governed by the ministry of telecommunications. Using one (or one of several) Internet exchange points in your country, the connection is routed to the global Internet.
Whether you are accessing the Internet from your home computer or from a mobile phone on a moving train, the principle remains the same: your device connects to the local ISP > connects to the national provider > connects to the Internet exchange (backbone). Should you be visiting a website or sending an email to a server located in a different country (quite likely) then this progression through the network hierarchy is repeated on the other end side of the communications channel too.
Notice that in the last example, your connection routes through at least two national (legal) jurisdictions.
Exercise: Use a Geo-IP traceroute tool (http://traceroute.monitis.com/ ) to view how your connection is routed to a particular website.
Note: The Internet is a packet-switching network. This means that your email, for example, is broken down into small individual packets which are then sent independently of each other along the many possible routes on the network that connect you to your friend's computer. These packets are then reassembled at the receiver's end to re-create your email. Important! You do not control how data travels through the Internet once you hit the send button.
Locate
Now that you're connected, let's discuss what happens when you request to open a particular website and how this site then delivers back to your computer. Numerous protocols and technical standards govern how the Internet and all of its users locate and communicate with each other. The most important of which we will discuss has to do with Internet addressing. Because everyone on the Internet adheres to these, you are able to open webiste.com and send an email from your computer to a friend's mobile phone in another country.
Internet Protocol (IP) Address
Internet routing is possible because every computer is uniquely identified on the network by what is known as an IP address. These addresses look like 83.169.39.231 and are the building blocks of Internet addressing. Whenever you want to open a website from your computer, the Internet needs to know your IP address and the IP address of the server the website is hosted on, to make the connection. Important! Your IP address is assigned to you by your local ISP or if you are using mobile Internet, by your telecommunications provider. In most countries ISPs are obligated by law to collect and store traffic data (which IP requested a connection to which IP and when) . This is used primarily for identifying user activity on the Internet at a later date and is the main tool in the hands of Internet police.
Note: in an office or Internet cafe scenario, only one computer is connected to the Internet and all other computers connect through it. Only the Internet facing computer (modem) is assigned an external IP address, whilst the others are assigned an internal IP address. Browsing history made from a computer in an Internet café can be traced back by the ISP to the café, not to the individual's computer.
Exercise: Find your current IP on the Internet
- View your computer's IP by visiting http://hostip.info You can also view the IP addresses associated with your favourite websites through this system.
- Next, go to http://whois.net/ to find out who that particular IP address is registered to.
Domain Name System
Even though all computers connected to the Internet are assigned an IP address, we usually do not know these addresses nor do we use them when opening a website. Numbers are quite difficult to remember (how many phone numbers do you know by heart?) and for this reason we assign names as addresses for our websites (also known as a Universal Resource Locator – URL). These names and their associated IP addresses are recorded in the Domain Name System (DNS). This is akin to the Internet's telephone directory and is another critical component of Internet routing and operations. DNS is hierarchical, meaning that your computer can have its list of URLs and corresponding IPs, your ISP will have a list, the national provider will have a list and so on, right up to the root DNS servers (of which there are 13). Should your computer not have an entry for www.livejournal.com it will ask the next list up in line – the ISP's and so on. Whether browsing websites or sending email, DNS always plays a part. Below is a diagram describing how DNS is utilized when you search for the LiveJournal website.
- Not knowing the LiveJournal address, you open Google naturally. Your computer doesn't know where www.google.com is and so asks the DNS server for Google's IP.
- Using Google's IP you locate the search engine and punch in 'LiveJournal'. The search returns www.livejournal.com which you promptly click.
- Once again, your computer has no idea where to locate www.livejournal.com and returns to the DNS server to get its IP.
- Finally, using the correct IP you can access LiveJournal's website.
Media: A brief explanation how websites are located using the DNS.
Another video that discusses the regulative and technical framework behind DNS and why this is important.
Exercise: Change your computer's DNS settings (Here is a walkthrough regarding changing DNS settings in Windows 7)
- Use the http://hostip.info tool to find out the IP addresses of your favourite websites.
- Open the Control Panel and locate your Network Connection settings (LAN or Wireless).
- Manually set the DNS servers to OpenDNS addresses:
208.67.222.222 208.67.220.220
or use two of the root DNS servers http://en.wikipedia.org/wiki/Root_name_server ).
Interact
The last part of the Internet's infrastructure concerns the applications we use to send and receive content on the Internet. These include your browser, email program, chat client and every other software on your computer that utilizes or help you interact on the Internet. Every application has its particular language and protocols and these often affect how information is transmitted between two computers on the Internet. This usually involves a type of technical language (protocol) by which it communicates or the channel (port) it selects for communication. For example, some applications send data in a clear-text format and every computer/router that stands in-between the communicating parties can access and understand the transmitted information. Other applications take special care to ensure privacy for the communicating parties. For example, when you connect to http://google.com your browser is using the 'http' protocol on port 80. However when the website's address is preceded by the letters 'https' (https://mail.google.com) your browser begins to use the Secure Sockets Layer (SSL) protocol on port 443. The majority of this course is explaining and exploring the different ways that applications interact on the Internet, directly impacting upon your privacy, anonymity and authentication of the transmitted message.
Media: Here's a video tutorial from some kid in his bedroom, pulling all the topics that we have discussed above, together.