Difference between revisions of "Internet Censorship"
(Created page with "Research carried out by organisations like the OpenNet Initiative (ONI), https://www.herdict.org and others indicates that many countries filter a wide variety of social, poli...") |
|||
| (4 intermediate revisions by the same user not shown) | |||
| Line 3: | Line 3: | ||
Varying in costs and point of installation, all website censorship systems operate on a similar principle. Requests made by the user for a particular website or content are checked against a list of banned addresses or keywords. Five common methods to block Internet content are practised today and described below. Methods to bypass these restrictions, also known as circumvention are discussed in 'the following module. | Varying in costs and point of installation, all website censorship systems operate on a similar principle. Requests made by the user for a particular website or content are checked against a list of banned addresses or keywords. Five common methods to block Internet content are practised today and described below. Methods to bypass these restrictions, also known as circumvention are discussed in 'the following module. | ||
| − | Exercise: Take a look at blocked website's around the world at this moment from https://www.herdict.org/# | + | '''Exercise:''' Take a look at blocked website's around the world at this moment from https://www.herdict.org/# |
| − | Media: The Berkman Center for Internet and Society describe the various way to filter content request or delivery | + | '''Media:''' The Berkman Center for Internet and Society describe the various way to filter content request or delivery |
| − | + | {{#ev:youtube|LAUH5MbXc94}} | |
| − | How websites are blocked | + | ===How websites are blocked=== |
This section requires that you have read and understood Lesson 1. The Internet and its Pitfalls, in particular the bits on Internet Protocol (IP) and the Domain Name System (DNS). | This section requires that you have read and understood Lesson 1. The Internet and its Pitfalls, in particular the bits on Internet Protocol (IP) and the Domain Name System (DNS). | ||
| Line 17: | Line 17: | ||
These blocklists contain forbidden website addresses, for example www.hrw.org or www.tol.org A request for websites found in this list will be denied. | These blocklists contain forbidden website addresses, for example www.hrw.org or www.tol.org A request for websites found in this list will be denied. | ||
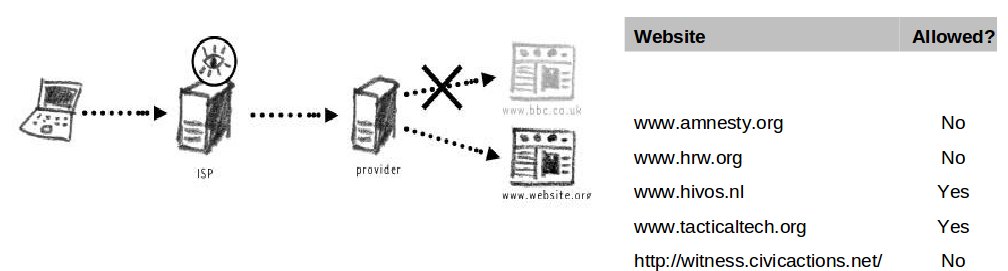
| − | URL Blocking | + | '''URL Blocking''' |
The most common way to block access to a particular website is by adding its name (the universal resource locator) to the banned list. | The most common way to block access to a particular website is by adding its name (the universal resource locator) to the banned list. | ||
| − | + | [[File:URLblocking.jpg|URL Blocking]] | |
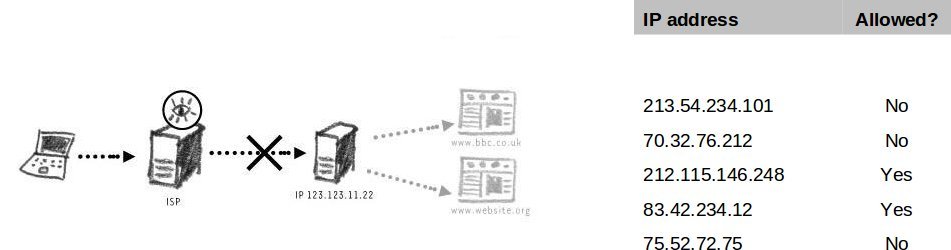
| − | IP Banning | + | '''IP Banning''' |
Every website is associated with a unique IP of the computer it is hosted on. Should the censor wish to ban access to livejournal.com using the IP address of the server it is hosted on, a simple query on the Internet will show that it is 208.93.0.128. This address will be added to the banned list and interrupt connections destined for that IP. | Every website is associated with a unique IP of the computer it is hosted on. Should the censor wish to ban access to livejournal.com using the IP address of the server it is hosted on, a simple query on the Internet will show that it is 208.93.0.128. This address will be added to the banned list and interrupt connections destined for that IP. | ||
| − | + | [[File:IPbanning.jpg|IP banning]] | |
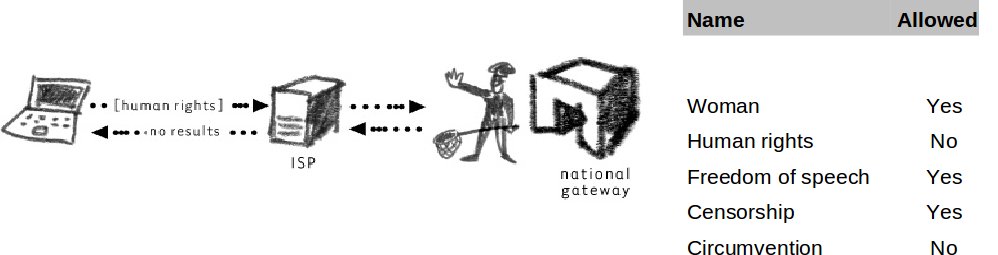
| − | + | '''Keyword Filtering''' | |
| − | Keyword Filtering | + | |
Often, the censor is interested in blocking particular content on the Internet and all websites bearing this content should be added to the blocklists. For example, this may relate to recent news or topics identified by particular keywords (e.g. Tienanmen Square massacre). The most efficient way (from the censor's point of view) to achieve this is through keyword filtering. On the routers at the ISP or the national gateway, content is filtered as it passes through the infrastructure. As soon as a particular string of characters (keywords) is noticed, the system raises a flag and either terminates the connection or simply reports the user's IP address. Keyword filtering may be activated on outgoing connections (you searching for something on Google) or incoming data (accessing a website that contains the keywords in its text). | Often, the censor is interested in blocking particular content on the Internet and all websites bearing this content should be added to the blocklists. For example, this may relate to recent news or topics identified by particular keywords (e.g. Tienanmen Square massacre). The most efficient way (from the censor's point of view) to achieve this is through keyword filtering. On the routers at the ISP or the national gateway, content is filtered as it passes through the infrastructure. As soon as a particular string of characters (keywords) is noticed, the system raises a flag and either terminates the connection or simply reports the user's IP address. Keyword filtering may be activated on outgoing connections (you searching for something on Google) or incoming data (accessing a website that contains the keywords in its text). | ||
| − | + | [[File:Keywordfiltering.jpg|Keyword filtering]] | |
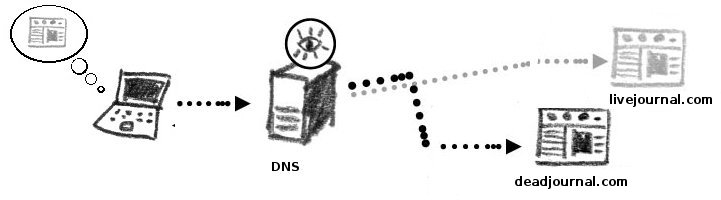
| − | DNS tampering | + | '''DNS tampering''' |
Another method to prevent users visiting websites is to tamper with the local (ISP or national gateway) copy of the DNS record. This results in requests for “www.livejournal.com” being forwarded to an unrelated (sometimes especially prepared) website. The caveat is that the user's computer (and often the user himself) is not aware of this redirection as the website's URL appears correctly in their browser. | Another method to prevent users visiting websites is to tamper with the local (ISP or national gateway) copy of the DNS record. This results in requests for “www.livejournal.com” being forwarded to an unrelated (sometimes especially prepared) website. The caveat is that the user's computer (and often the user himself) is not aware of this redirection as the website's URL appears correctly in their browser. | ||
| − | + | [[File:DNStampering.jpg|DNS Tampering]] | |
| − | Protocol, port filtering & bandwidth | + | '''Protocol, port filtering & bandwidth restrictions''' |
A recent addition to the censor's toolkit is filtering requests according to a particular protocol (e.g. SSL) or to the port number used by a particular protocol (e.g. 443). Countries that want to ban secure communications on the Internet sometimes implement this type of filtering even at the expense of not being able to use it themselves. During a recent election period in Belarus, connections to foreign websites were restricted by limiting the capacity (bandwidth) of the channel connecting the national gateway to the Internet. All it took was a few users in the country to fill-up the reduced channel completely, making everyone else's access impossible. | A recent addition to the censor's toolkit is filtering requests according to a particular protocol (e.g. SSL) or to the port number used by a particular protocol (e.g. 443). Countries that want to ban secure communications on the Internet sometimes implement this type of filtering even at the expense of not being able to use it themselves. During a recent election period in Belarus, connections to foreign websites were restricted by limiting the capacity (bandwidth) of the channel connecting the national gateway to the Internet. All it took was a few users in the country to fill-up the reduced channel completely, making everyone else's access impossible. | ||
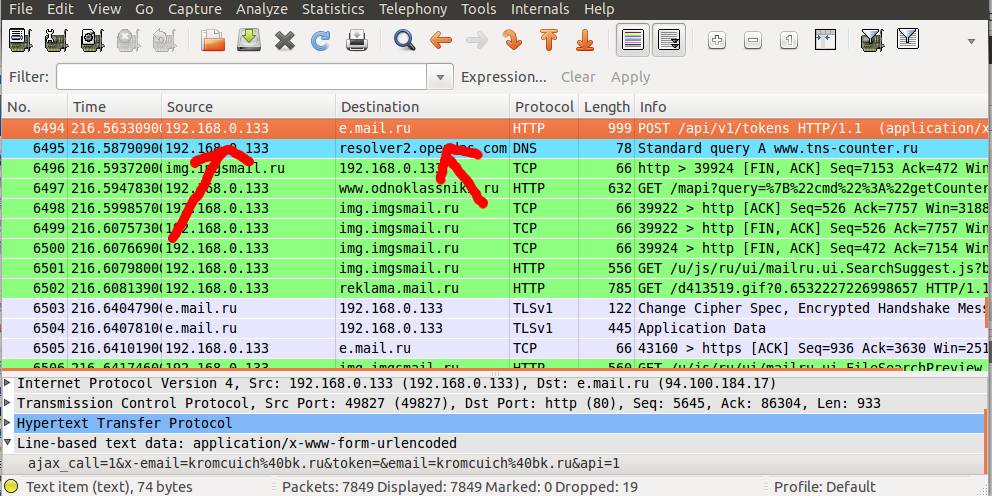
| − | + | [[File:IPrequesting.png|IP requesting]] | |
On this screenshot you can see the computer's IP requesting the domain e.mail.ru | On this screenshot you can see the computer's IP requesting the domain e.mail.ru | ||
| − | Media: Staff from the Berkman Center for Internet and Society talk about the reasons and politics behind Internet censorship | + | '''Media:''' Staff from the Berkman Center for Internet and Society talk about the reasons and politics behind Internet censorship |
| − | + | {{#ev:youtube|HfS_2oXVch0}} | |
| − | What happens when a site is blocked? | + | '''What happens when a site is blocked?''' |
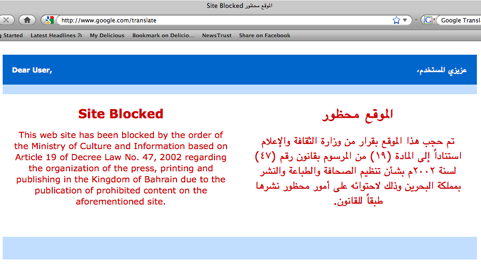
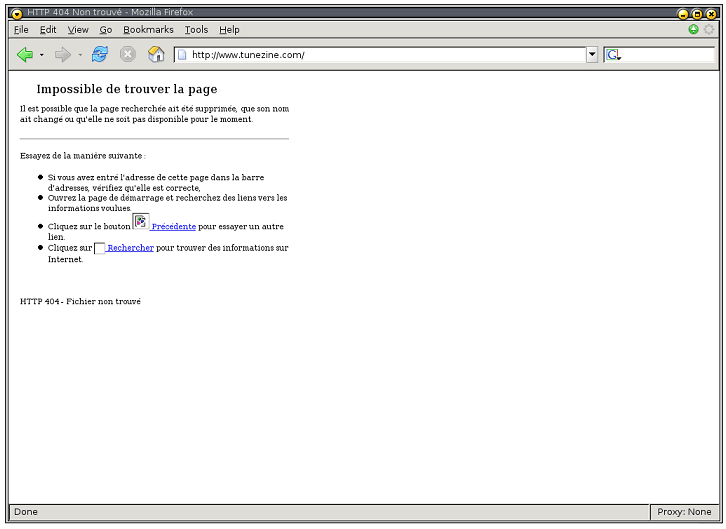
Actually the answer to this question depends on who is doing the blocking. In some countries users are told when access to a certain website is restricted (sometimes they are also told why, e.g. article of law). In other places, you may simply receive an error, as if you had misspelled the website name or that the address simply doesn't exist. | Actually the answer to this question depends on who is doing the blocking. In some countries users are told when access to a certain website is restricted (sometimes they are also told why, e.g. article of law). In other places, you may simply receive an error, as if you had misspelled the website name or that the address simply doesn't exist. | ||
| − | + | [[File:SiteBlocked3.png|Site Blocked 3]] | |
| + | |||
| − | + | [[File:blocksite23.png|blocksite 2 3]] | |
One easy way to figure out whether a website is being censored in your country (it may simply be malfunctioning) is to ask a friend in another country to access it. If they can and you cannot, it is reasonable to assume that this site has been added to the blocklists in your Internet jurisdiction. | One easy way to figure out whether a website is being censored in your country (it may simply be malfunctioning) is to ask a friend in another country to access it. If they can and you cannot, it is reasonable to assume that this site has been added to the blocklists in your Internet jurisdiction. | ||
Latest revision as of 19:17, 27 May 2014
Research carried out by organisations like the OpenNet Initiative (ONI), https://www.herdict.org and others indicates that many countries filter a wide variety of social, political and 'national security' content, while rarely publishing precise lists of what has been blocked. Naturally, those who wish to control their citizens' access to the Internet also make a special effort to block known proxies and websites that offer tools and instruction to help people circumvent these filters.
Varying in costs and point of installation, all website censorship systems operate on a similar principle. Requests made by the user for a particular website or content are checked against a list of banned addresses or keywords. Five common methods to block Internet content are practised today and described below. Methods to bypass these restrictions, also known as circumvention are discussed in 'the following module.
Exercise: Take a look at blocked website's around the world at this moment from https://www.herdict.org/#
Media: The Berkman Center for Internet and Society describe the various way to filter content request or delivery
How websites are blocked
This section requires that you have read and understood Lesson 1. The Internet and its Pitfalls, in particular the bits on Internet Protocol (IP) and the Domain Name System (DNS).
Website censorship or the filtering of your website requests is based on blocklists. Whenever your request matches one of the entries on the blocklist, the connection is denied or re-routed. These blocklists may exist at your local network, at the ISP or the national gateway. It may even be a combination of various blocklists at all stages in the national Internet infrastructure, as is the case for example in China. Blocklists may contain the following information.
These blocklists contain forbidden website addresses, for example www.hrw.org or www.tol.org A request for websites found in this list will be denied.
URL Blocking
The most common way to block access to a particular website is by adding its name (the universal resource locator) to the banned list.
IP Banning
Every website is associated with a unique IP of the computer it is hosted on. Should the censor wish to ban access to livejournal.com using the IP address of the server it is hosted on, a simple query on the Internet will show that it is 208.93.0.128. This address will be added to the banned list and interrupt connections destined for that IP.
Keyword Filtering
Often, the censor is interested in blocking particular content on the Internet and all websites bearing this content should be added to the blocklists. For example, this may relate to recent news or topics identified by particular keywords (e.g. Tienanmen Square massacre). The most efficient way (from the censor's point of view) to achieve this is through keyword filtering. On the routers at the ISP or the national gateway, content is filtered as it passes through the infrastructure. As soon as a particular string of characters (keywords) is noticed, the system raises a flag and either terminates the connection or simply reports the user's IP address. Keyword filtering may be activated on outgoing connections (you searching for something on Google) or incoming data (accessing a website that contains the keywords in its text).
DNS tampering
Another method to prevent users visiting websites is to tamper with the local (ISP or national gateway) copy of the DNS record. This results in requests for “www.livejournal.com” being forwarded to an unrelated (sometimes especially prepared) website. The caveat is that the user's computer (and often the user himself) is not aware of this redirection as the website's URL appears correctly in their browser.
Protocol, port filtering & bandwidth restrictions
A recent addition to the censor's toolkit is filtering requests according to a particular protocol (e.g. SSL) or to the port number used by a particular protocol (e.g. 443). Countries that want to ban secure communications on the Internet sometimes implement this type of filtering even at the expense of not being able to use it themselves. During a recent election period in Belarus, connections to foreign websites were restricted by limiting the capacity (bandwidth) of the channel connecting the national gateway to the Internet. All it took was a few users in the country to fill-up the reduced channel completely, making everyone else's access impossible.
On this screenshot you can see the computer's IP requesting the domain e.mail.ru
Media: Staff from the Berkman Center for Internet and Society talk about the reasons and politics behind Internet censorship
What happens when a site is blocked?
Actually the answer to this question depends on who is doing the blocking. In some countries users are told when access to a certain website is restricted (sometimes they are also told why, e.g. article of law). In other places, you may simply receive an error, as if you had misspelled the website name or that the address simply doesn't exist.
One easy way to figure out whether a website is being censored in your country (it may simply be malfunctioning) is to ask a friend in another country to access it. If they can and you cannot, it is reasonable to assume that this site has been added to the blocklists in your Internet jurisdiction.