Difference between revisions of "What is Internet surveillance?"
| (14 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
| − | As discussed in the previous section, we cannot affect the manner in which our content is routed around the Internet and are simply left a choice between the various applications to use for sending and receiving data. On its way to the recipient, our messages | + | =Internet Surveillance= |
| + | |||
| + | As discussed in the previous section, we cannot affect the manner in which our content is routed around the Internet and are simply left a choice between the various applications to use for sending and receiving data. On its way to the recipient, our messages passes through multiple servers, routers and any other hardware corporations and governments choose to put into the network. At each of these points on the network, our data is processed as it passes from one server to the next and becomes accessible to whoever controls that particular piece of hardware. In fact, the possibility for surveillance is built into the network and Internet communications can be seen as the 21st century's postal system – where your letter is dropped into a post box, picked up by the mailman, processed at the post facility, shipped to its destination, processed by the post facility over there, given to the mailman and delivered to the recipient. At any one of those steps your message can be read. Our 'postal guarantee' against this intrusion is the sealed envelope. Other methods exist on the Internet and are described in Lesson 2. | ||
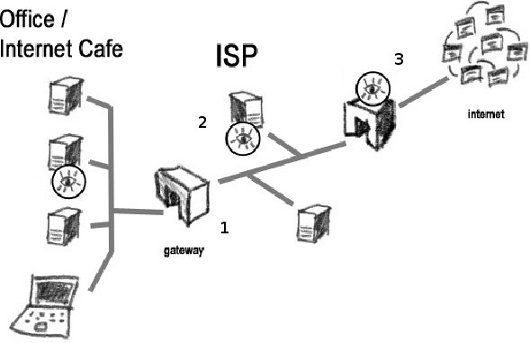
Let's have look at the pathways taken by an email message you send as it leaves your national Internet infrastructure, and where it is exposed to surveillance. | Let's have look at the pathways taken by an email message you send as it leaves your national Internet infrastructure, and where it is exposed to surveillance. | ||
| − | |||
| Line 9: | Line 10: | ||
| − | + | ==The local network== | |
Whether you are connecting to the Internet from home, office, Internet cafe or another location, the first point of call for your email on its way to the recipient is the local modem – the one which is connected to the Internet. Whoever has access to this modem will be able to view the network's traffic as it is sent and received from the Internet. | Whether you are connecting to the Internet from home, office, Internet cafe or another location, the first point of call for your email on its way to the recipient is the local modem – the one which is connected to the Internet. Whoever has access to this modem will be able to view the network's traffic as it is sent and received from the Internet. | ||
| − | Exercise: Install the Wireshark network protocol analyzer (http://www.wireshark.org/) to view traffic on the local network (this exercise is only for those using a cable connection to the modem/router/network). | + | '''Exercise:''' Install the Wireshark network protocol analyzer (http://www.wireshark.org/) to view traffic on the local network (this exercise is only for those using a cable connection to the modem/router/network). |
| − | Demonstration: | + | '''Demonstration: ''' |
| + | {{#ev:youtube|lVutDlIUNOg}} | ||
| − | |||
| + | '''Note:''' Open wireless networks (those that do not require a password to connect) are just as vulnerable to surveillance by anyone connected to the same wireless router. They present an even greater risk since anyone within range can connect. Wireless networks protected by a password present a much greater challenge, since everyone's connection to the router is encrypted with an individual session key. You should be using a long WPA2 standard password (as opposed to a WEP key) and if your router doesn't have that option – time to upgrade! | ||
| − | + | ==The Internet Service Provider== | |
| − | + | ||
| − | + | ||
| − | + | ||
The local ISP plays the role of a postman for your Internet connection. He delivers and collects all of your communications with the Internet. He assigns your computer its IP address and can keep a log of your online activities (often by law). The ISP manages and has access to the traffic data of all its clients. Internet surveillance and censorship is often implemented at the ISP level. In many countries users are offered a choice between different ISPs and should consider the company's privacy and data retention policies when doing so. | The local ISP plays the role of a postman for your Internet connection. He delivers and collects all of your communications with the Internet. He assigns your computer its IP address and can keep a log of your online activities (often by law). The ISP manages and has access to the traffic data of all its clients. Internet surveillance and censorship is often implemented at the ISP level. In many countries users are offered a choice between different ISPs and should consider the company's privacy and data retention policies when doing so. | ||
| − | + | ==The National Gateway== | |
Every country needs to manage its entry and exit points to the Internet. Usually this is done by large telecommunications providers operating according to national legislation. Sometimes these gateways are run and managed by the ministry of communications directly. These gateways have access to national traffic data and some countries implement Internet surveillance and censorship at this level. | Every country needs to manage its entry and exit points to the Internet. Usually this is done by large telecommunications providers operating according to national legislation. Sometimes these gateways are run and managed by the ministry of communications directly. These gateways have access to national traffic data and some countries implement Internet surveillance and censorship at this level. | ||
Modern Internet surveillance (or monitoring) is done by software looking for specific keywords or phrases. This is known as flagging. Whenever a particular keyword passes through the infrastructure, the IP address of the sender is recorded along with the message. Flagging could also react to requests for certain websites. In a targeted surveillance scenario, a particular IP could be singled out for monitoring and all of its activity recorded. | Modern Internet surveillance (or monitoring) is done by software looking for specific keywords or phrases. This is known as flagging. Whenever a particular keyword passes through the infrastructure, the IP address of the sender is recorded along with the message. Flagging could also react to requests for certain websites. In a targeted surveillance scenario, a particular IP could be singled out for monitoring and all of its activity recorded. | ||
| Line 33: | Line 32: | ||
| − | + | [[File:logindetails.png|600px|Login Details]] | |
| − | + | ||
| − | [[File:logindetails.png|Login Details]] | + | |
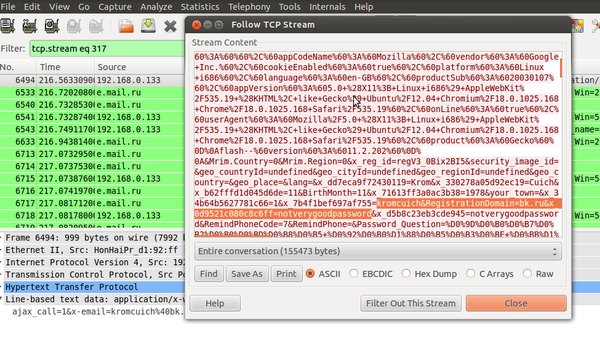
Here you can see login and password details being transmitted on the Internet. Every router located between the user's computer and the website being visited has access to this data. | Here you can see login and password details being transmitted on the Internet. Every router located between the user's computer and the website being visited has access to this data. | ||
| − | Media: A very interesting (if slightly lengthy) DEFCON lecture explaining the implementation of Internet surveillance on commercial and government levels | + | '''Media:''' A very interesting (if slightly lengthy) DEFCON lecture explaining the implementation of Internet surveillance on commercial and government levels. |
| − | + | ||
| − | + | {{#ev:youtube|jJDCxzKmROY}} | |
Latest revision as of 22:20, 8 May 2014
Contents
Internet Surveillance
As discussed in the previous section, we cannot affect the manner in which our content is routed around the Internet and are simply left a choice between the various applications to use for sending and receiving data. On its way to the recipient, our messages passes through multiple servers, routers and any other hardware corporations and governments choose to put into the network. At each of these points on the network, our data is processed as it passes from one server to the next and becomes accessible to whoever controls that particular piece of hardware. In fact, the possibility for surveillance is built into the network and Internet communications can be seen as the 21st century's postal system – where your letter is dropped into a post box, picked up by the mailman, processed at the post facility, shipped to its destination, processed by the post facility over there, given to the mailman and delivered to the recipient. At any one of those steps your message can be read. Our 'postal guarantee' against this intrusion is the sealed envelope. Other methods exist on the Internet and are described in Lesson 2.
Let's have look at the pathways taken by an email message you send as it leaves your national Internet infrastructure, and where it is exposed to surveillance.
The local network
Whether you are connecting to the Internet from home, office, Internet cafe or another location, the first point of call for your email on its way to the recipient is the local modem – the one which is connected to the Internet. Whoever has access to this modem will be able to view the network's traffic as it is sent and received from the Internet.
Exercise: Install the Wireshark network protocol analyzer (http://www.wireshark.org/) to view traffic on the local network (this exercise is only for those using a cable connection to the modem/router/network).
Demonstration:
Note: Open wireless networks (those that do not require a password to connect) are just as vulnerable to surveillance by anyone connected to the same wireless router. They present an even greater risk since anyone within range can connect. Wireless networks protected by a password present a much greater challenge, since everyone's connection to the router is encrypted with an individual session key. You should be using a long WPA2 standard password (as opposed to a WEP key) and if your router doesn't have that option – time to upgrade!
The Internet Service Provider
The local ISP plays the role of a postman for your Internet connection. He delivers and collects all of your communications with the Internet. He assigns your computer its IP address and can keep a log of your online activities (often by law). The ISP manages and has access to the traffic data of all its clients. Internet surveillance and censorship is often implemented at the ISP level. In many countries users are offered a choice between different ISPs and should consider the company's privacy and data retention policies when doing so.
The National Gateway
Every country needs to manage its entry and exit points to the Internet. Usually this is done by large telecommunications providers operating according to national legislation. Sometimes these gateways are run and managed by the ministry of communications directly. These gateways have access to national traffic data and some countries implement Internet surveillance and censorship at this level. Modern Internet surveillance (or monitoring) is done by software looking for specific keywords or phrases. This is known as flagging. Whenever a particular keyword passes through the infrastructure, the IP address of the sender is recorded along with the message. Flagging could also react to requests for certain websites. In a targeted surveillance scenario, a particular IP could be singled out for monitoring and all of its activity recorded. Note: When you are using a satellite Internet connection, your bypass the national infrastructure. The satellite relays your connection to a ground station usually located in another country (depending on your choice of providers). Communications between the satellite and your receiver antenna are encrypted by default. For this reason, many authoritarian states forbid satellite Internet connections and by using advanced equipment can locate the transmitter.
Here you can see login and password details being transmitted on the Internet. Every router located between the user's computer and the website being visited has access to this data.
Media: A very interesting (if slightly lengthy) DEFCON lecture explaining the implementation of Internet surveillance on commercial and government levels.